ꓘamerka
How it works
Pick devices
Choose from more than 100+ devices based on Shodan dorks
Gather information
Collect passive information from Shodan, WHOISXML and Binary Edge
Geolocate
Based on device response and other information pinpoint it to speccific location
Scan
Scan actively device with NMAP modules
Test
Run exploit against device or try default credentials
Report
Report vulnerable device in critical infrastructure to your local CERT
Security
Best practices
Exposure
Continually monitor and assess the security of ICS, networks, and inter-connections
Credentials
Use strong and different passwords for each device to prevent bruteforcing attacks
Update
Enable available security features and implement robust configuration management practices
Training
Provide ICS cybersecurity training for all operators and administrators
Security
Implement a risk-based defense-in-depth approach to securing ICS hosts and networks
Inventory
Maintain ICS asset inventory of all hardware, software, and supporting infrastructure technologies
ꓘamerka
Features

100+ devices
Choose from more than 100 devices including Industrial Control System, Internet of Things or medical devices.

Geolocate
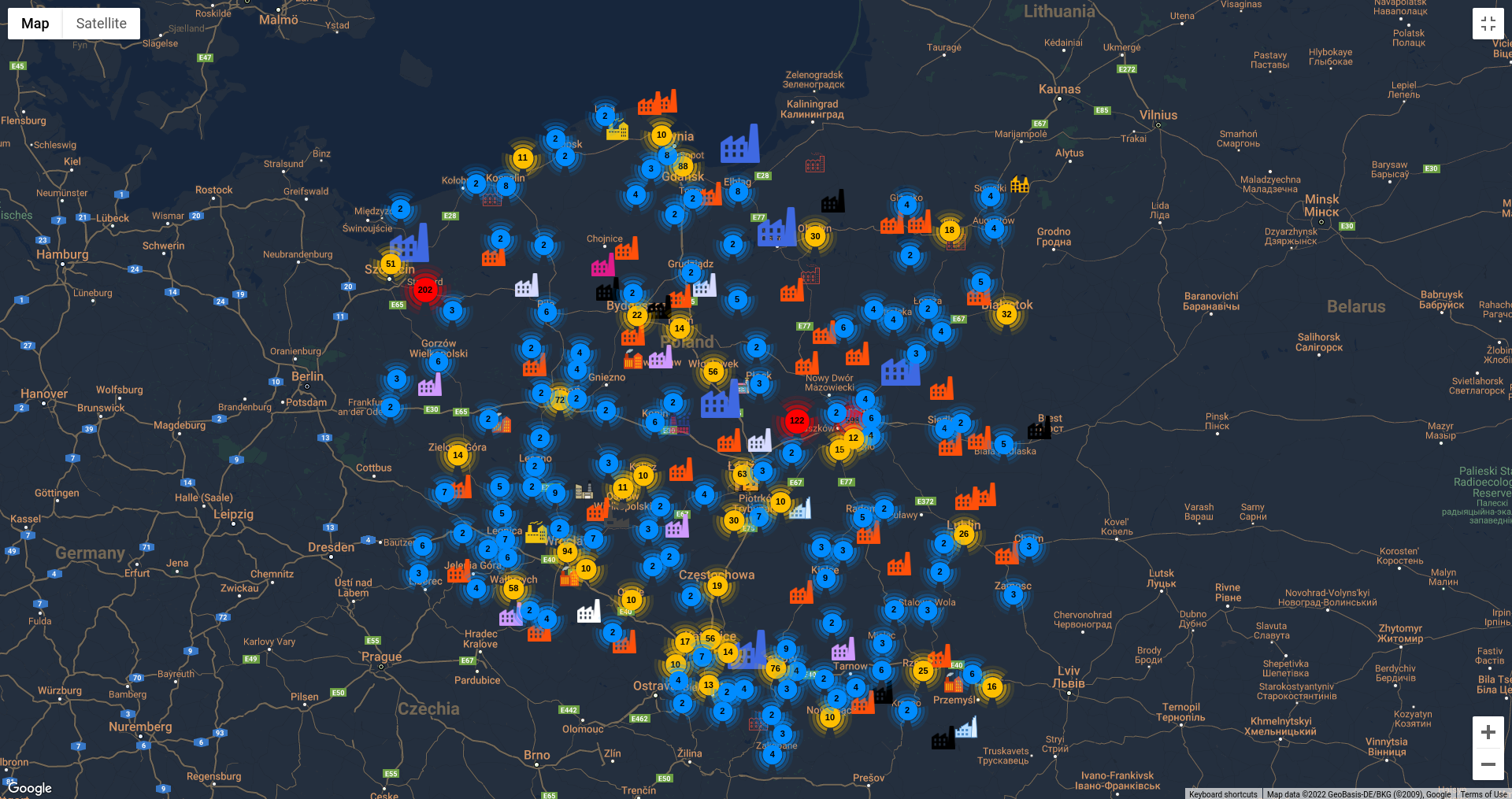
Thanks to indicators from device, pinpoint each one to specific facility including critical infrastructure

Details
Access details about devices including open ports, screenshot or even WHOIS information

Active scan
Scan with NMAP and run specific modules to identify the device

Test
Implement and run exploit against the target straight from application
Statistics
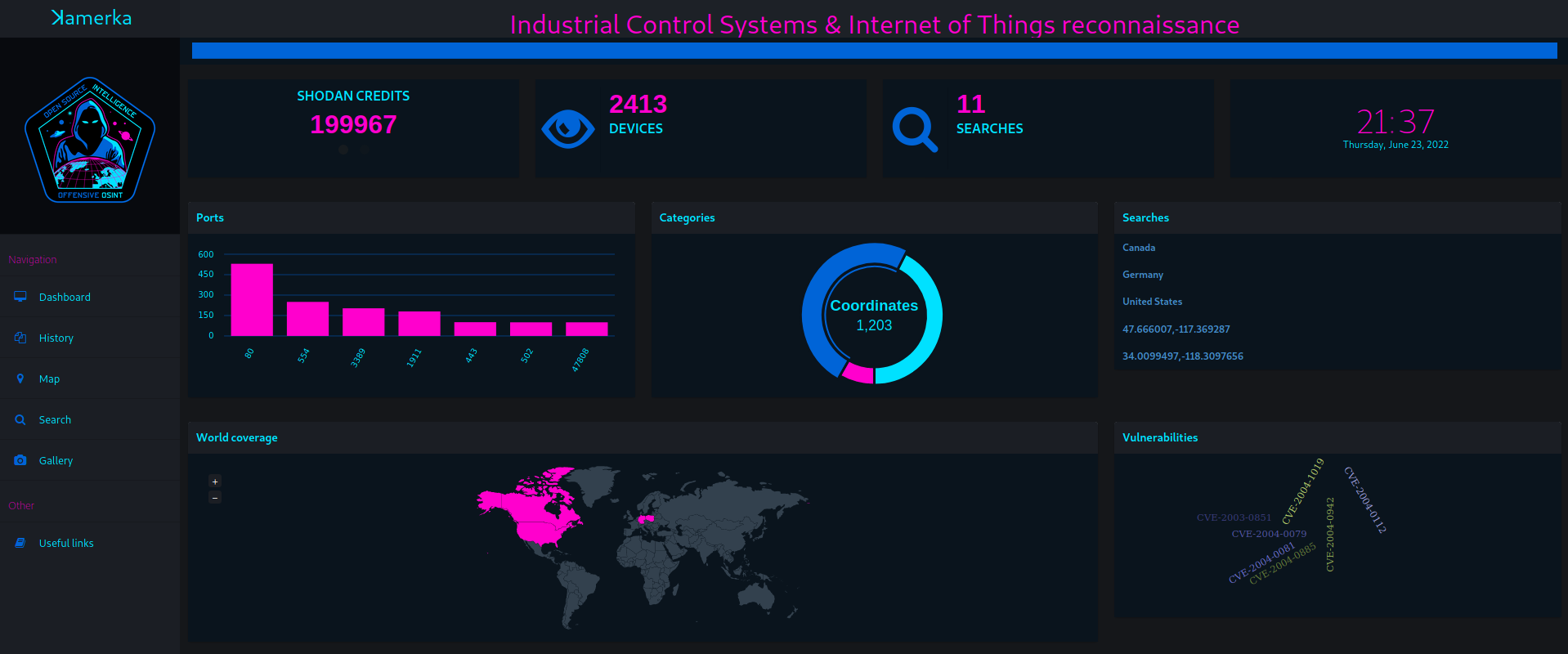
Access statistics for your search (ports, cities, type of device and more)
Faqs
Frequently Asked Questions
Detailed description and tool is available on https://github.com/woj-ciech/Kamerka-GUI
You need to have paid Shodan account, Google Maps key and optionally WHOISXML and Binary Edge API
Kamerka support 100+ different devices or protocols. You can find Human Machine Interface, ships, cameras, wind turbines, building operation workstations and many many more
Send an email to your local cert with all the details so they can contact the owner and limit the exposure
It may happen, please create an issue on Github.
Monitoring exposure of ICS and IoT devices are crucial for security and prevents easy access to the device
Kamerka
Screens
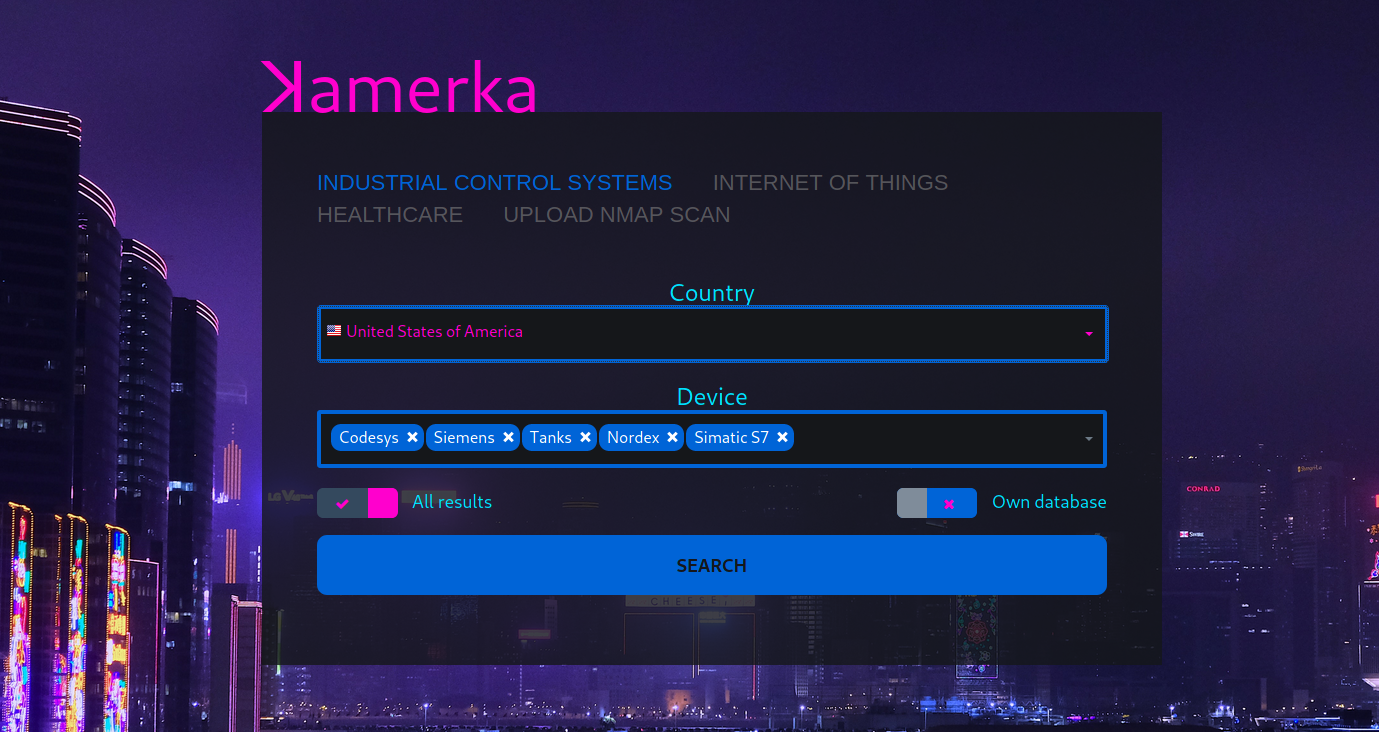
Search
Dashboard
Country map
Device details
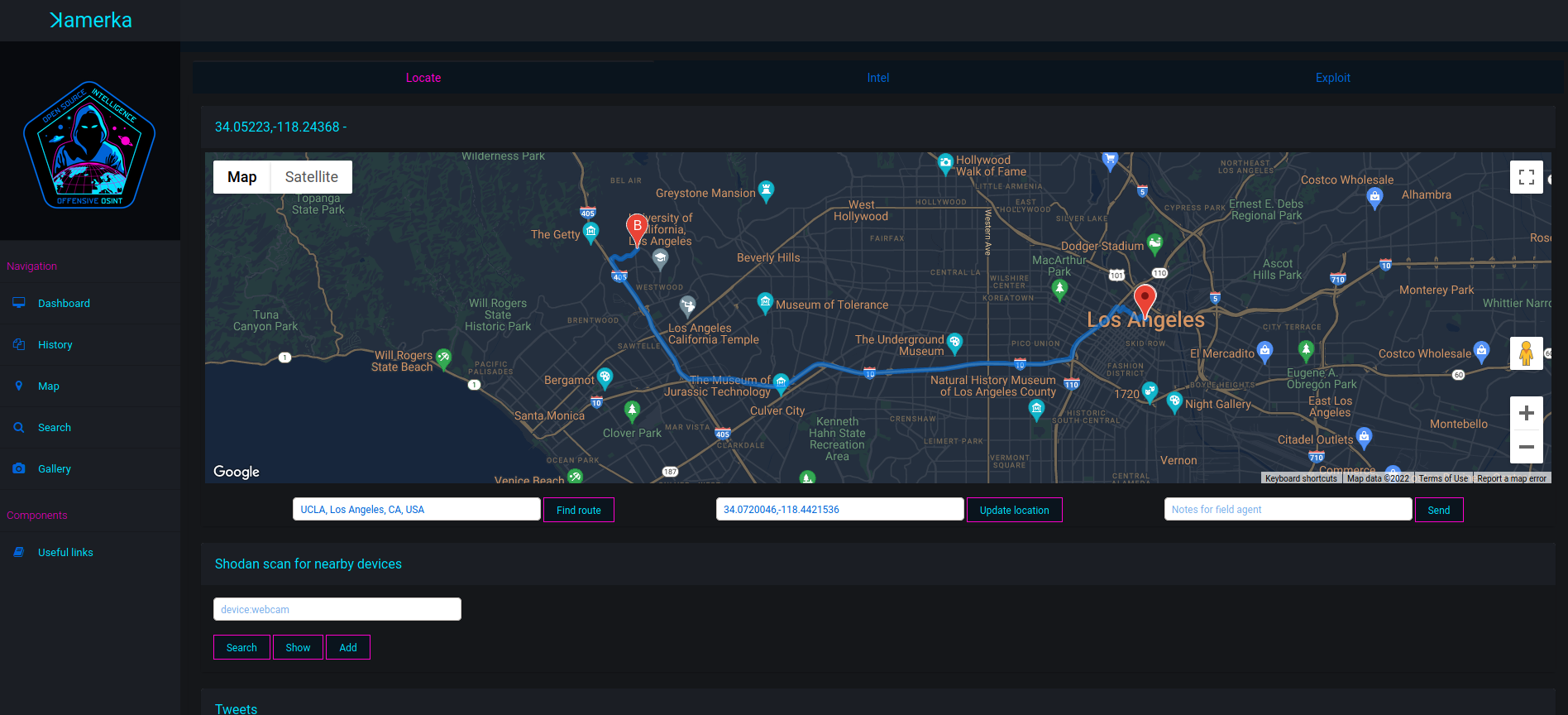
Intel

Geolocate

Scan & Exploit



